Organization identifiers are a key component of the ORCID vision: the ability and responsibility for employers of researchers to assert affiliation, associating the person’s ORCID iD with the organization iD and stamping that relationship with a provenance link. That assertion, in turn, can be shared by the researcher as they interact with publishers, funders, and other organizations they are affiliated with.
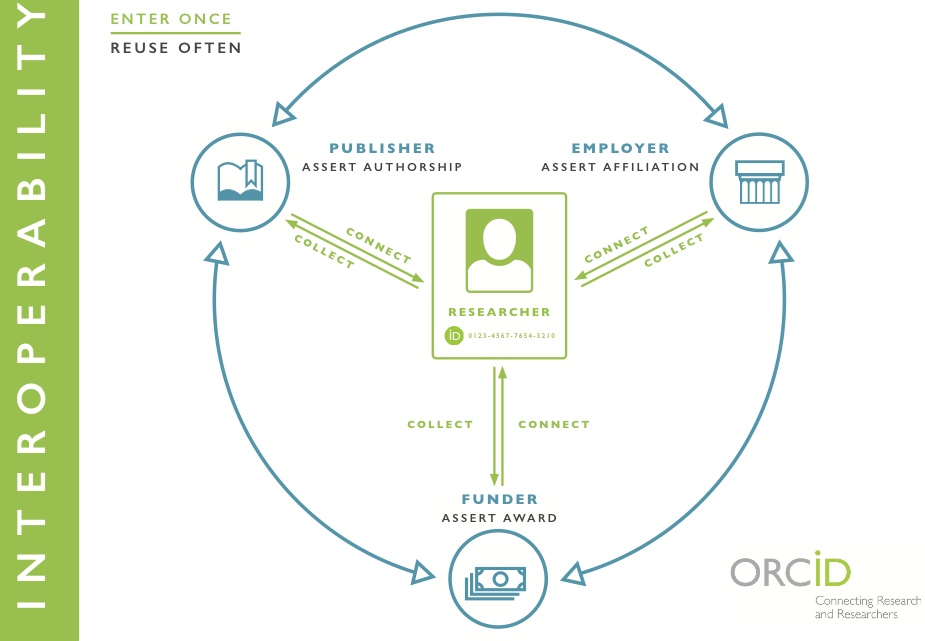
We have been using organization identifiers since 2013, when we launched the affiliations module that allowed individuals to self-claim their educational and employer organizations. In 2014, we launched the ORCID funding module, which allowed individuals to self-claim funding either directly or by searching the UberWizard funding registry. We have been using organization identifiers from Ringgold and the Crossref Funder Registry to back up our affiliations and our funding modules.
A numb er of organizations, including Oxford University, are starting to use this functionality to request permissions to make employer assertions into a user’s ORCID record. Researchers are directed to a landing page to register for an ORCID iD and connect it to their organization. And then, after the researcher approves permissions, the organization uses ORCID API credentials to post affiliation information (“assert affiliation”) into the employee’s ORCID record – with “Source” clearly indicated. We currently are working on functionality to enable this assertion process when an individual uses their institutional credentials to log into ORCID.
er of organizations, including Oxford University, are starting to use this functionality to request permissions to make employer assertions into a user’s ORCID record. Researchers are directed to a landing page to register for an ORCID iD and connect it to their organization. And then, after the researcher approves permissions, the organization uses ORCID API credentials to post affiliation information (“assert affiliation”) into the employee’s ORCID record – with “Source” clearly indicated. We currently are working on functionality to enable this assertion process when an individual uses their institutional credentials to log into ORCID.

In turn, this ORCID functionality is generating increasing interest among researchers themselves, who want to use ORCID to manage their affiliation credentials as they interact with publisher and funder systems. This example tweet is from 29 September 2016.
In addition to this Registry functionality, ORCID uses organization identifiers in our back-office systems. As part of the on-boarding process, we ensure that each of our members has a Salesforce and a Ringgold identifier, and we use these identifiers to manage renewals and API credentials.
Following up on a conversation at the Research Data Alliance in 2015, and growing out of work on the THOR project, earlier this year, we started a collaboration with Crossref and Datacite to review the current work on organization identifiers and define our use cases as consumers of these identifiers. We wrote up a summary of our key observations and recommendations, and then met with the community at the CNI and FORCE16 meetings to ascertain if there was broader support for these use cases. We also met with a number of organization identifier providers.
Based on all of these discussions, we have developed three papers.
- Organization Identifier Provider Landscape https://doi.org/10.5438/4716 (PDF GDoc)
- Technical Considerations for an Organization Identifier Registry https://doi.org/10.5438/7885 (PDF GDoc)
- Organization Identifier Project: A Way Forward https://doi.org/10.5438/2906 (PDF GDoc)
We invite the community to comment on these papers both online (using the GDoc link provided), by email, and in person at PIDapalooza. To move the initiative forward, we will be forming a Community Working Group, with the goal of holding an initial meeting before the end of 2016. The Working Group’s main charge is to develop a plan to launch and sustain an open, independent, non-profit organization identifier registry to facilitate the disambiguation of researcher affiliations.
