We are sometimes asked “Why are researchers asked to sign in to their ORCID account when they make a connection?” or “Why can’t users just copy and paste their ORCID iD into a system?” There are two reasons why signing in is so important. Firstly, when a researcher signs in (or “authenticates”), they can choose what happens to their account – it keeps them in control of their own information. Secondly, once a researcher has signed in, the connections they make to their ORCID iD are more useful – to them and to anyone else who wants to see those connections.
Let’s start by looking at what information a connection actually contains. We’ll use an example of a common connection: a link between an author and a journal article.The author is identified with their ORCID iD, and the article is identified with a DOI. A simple “back of an envelope” sketch might help to explain what is going on…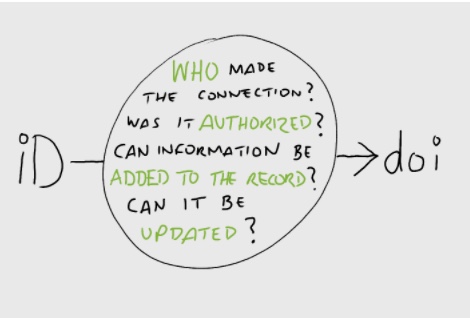
When the author has signed into their ORCID account to make the connection, they can choose to add their iD to the article. They can give permission for (or “authorize”) the journal to add information to their ORCID record, and they can give the journal permission to update their record if information about the publication changes. Anyone who looks at this connection can see how the connection was made, and who made it.
This information is what we mean when we talk about “provenance”.
Without signing in, there is no provenance information, as shown in the following sketch. 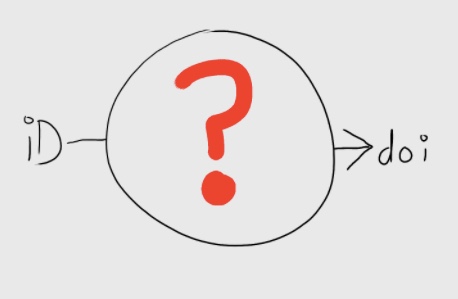
With no provenance, there is no way of knowing if you can trust the connection between (in this case) the researcher (the iD) and her/his work (the DOI). It may contain errors, or it may not belong to the author. Worse, this connection is closed – it cannot be used to add information to an ORCID record or supporting systems, nor can the publisher update it in the future if the information changes.
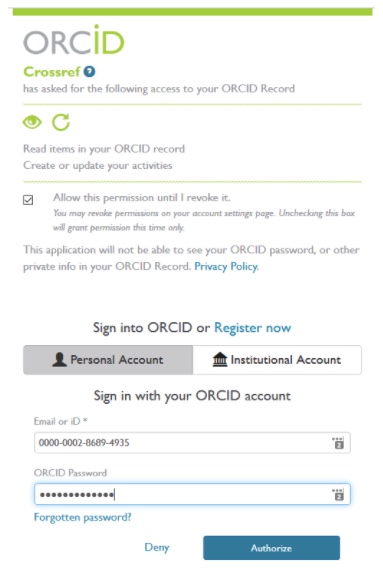 Signing in ensures the researcher has control over what connections are made to their iD and what happens to their ORCID record. We have worked hard to ensure researchers have this control; researcher control is one of our main principles. This means that organizations must ask for permission to use the individual’s iD or to add and update information in their record, or ask for access to read data available to trusted parties in their record.
Signing in ensures the researcher has control over what connections are made to their iD and what happens to their ORCID record. We have worked hard to ensure researchers have this control; researcher control is one of our main principles. This means that organizations must ask for permission to use the individual’s iD or to add and update information in their record, or ask for access to read data available to trusted parties in their record.
In addition to managing what is connected to their iD, researchers also decide how to share that information.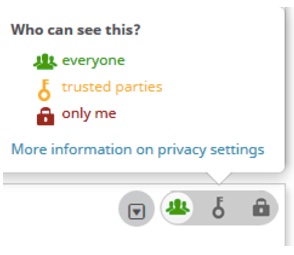
Information researchers mark as visible to “everyone” is available to the public. Other information can be made visible to “trusted parties” only, which means organizations must ask for permission to see it. Finally, researchers also have the option to mark items as visible to “only me” – private. They can do this for each individual item in their ORCID record, or set a default visibility for all their items.
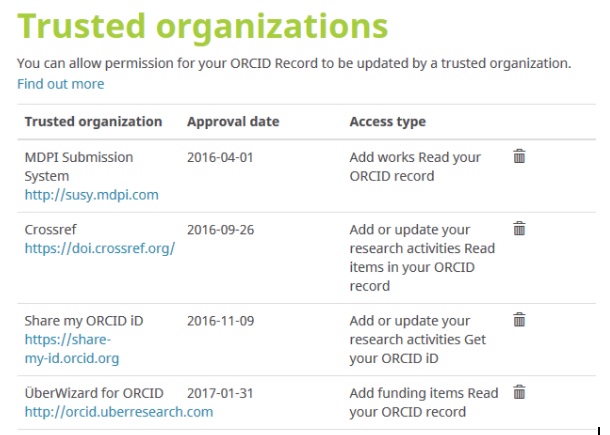
Asking for explicit permission to interact with a researcher’s record is best practice in data protection. You can find out more about what that means here. Researchers know who is asking for permission, and what exactly they are asking for permission to do. This means that they are giving informed consent before any information moves between systems. Researchers can see what permissions they have granted by looking at their account settings, and they can cancel permissions at any time. For more information, please see granting access to third-party organizations.
We mentioned trust already. Trust is very important to ORCID. In fact, it’s so important, we built a whole program around it. Researchers need to be able to trust us to look after their information, and to make it easy for them to control their record. Organizations need to be able to trust the iDs that they use and to ensure the information they’re connecting to an ORCID record is trustworthy. In turn, this will mean that everyone can trust this information.
The provenance information that is created when a researcher signs in (authenticates) is an essential part of trust. It shows which connections have been made. It means that the iD itself has been passed directly from one computer to another (using our API – you can find out more about the technical details of that here), so there are no typos or mistakes. Plus, iDs can only be authenticated by a researcher with the correct username and password for that iD, so you can be confident that permission was given by the account owner.
By using authentication, and connecting systems to ORCID using the API, our members protect researchers (by doing the right thing under data protection law, and by helping them to understand why and how their iD is being used) and they protect themselves by using secure, trusted connections. It helps everyone to be able to see if information about an article has come from the journal that published it, or if information about someone’s employment has come from their employer. We all have a responsibility to help make sure that the information we share is accurate, and that it is shared in a way that is useful to the community.
At ORCID, we think a lot about how we can help our members, and the more than 3 million researchers who have registered for an iD, to stay in control of their information. Authentication is one of the best tools we have to deliver that control to you, our community.
